Learn More About IPS and IDS!
What are IPS and IDS? Working in the field of cybersecurity, everyone is certainly familiar with these concepts. IDS systems were developed and applied to address issues such as preventing unauthorized intrusions and data theft... With today's cyber-attacks and security vulnerabilities, applying IPS systems to detect and prevent network risks is extremely effective. To learn more about the concept, role, and application of IPS, you should not miss the following article!
1. What is an IPS?
IPS stands for Intrusion Prevention System - a system that helps detect and prevent malicious activities on the network. IPS is considered an extended, enhanced version of the IDS (Intrusion Detection System) and operates by monitoring network and system traffic.
Currently, IPS systems are placed directly in the network path (inline), enabling them to block malicious attacks in real-time.
2. What are the main roles of IPS?
IPS is a crucial component of any modern enterprise security system. The use of multi-platform clouds in today's enterprises requires handling extremely large traffic volumes.
Therefore, manual monitoring or handling is nearly impossible. Additionally, the threats faced by today's enterprise security systems are increasingly numerous and complex. This is why IPS systems were developed, playing a key role in quickly and automatically responding to threats and attacks within the network.
If any malicious actions or suspicious traffic are detected, the IPS system will automatically perform one of the following actions:
- Terminate the exploited TCP session and completely block access to the violating IP address, user account, or destination server.
- Reset or reconfigure the firewall to prevent similar attacks in the future.
- Remove or replace any remaining malicious content on the network after attacks. This includes deleting header information and removing any infected attachments from files or email servers.
3. Common types of IPS today
There are several types of Intrusion Prevention Systems (IPS) for different purposes:
- Network-based Intrusion Prevention Systems (NIPS) are installed at strategic points to monitor and detect threats across the entire network traffic.
- Host-based Intrusion Prevention Systems (HIPS) are installed on a single endpoint system to monitor traffic to and from that specific host. This is considered the last line of defense when an attack bypasses the NIPS.
- Network Behavior Analysis (NBA) systems analyze network traffic to detect unusual activities, identifying threats such as distributed denial-of-service attacks, malware, and policy violations.
- Wireless Intrusion Prevention Systems (WIPS): These systems simply scan the WiFi network to filter unauthorized access and remove rogue devices from the network.
4. Significant benefits of IPS systems
Intrusion Prevention Systems (IPS) provide significant benefits in network safety and data security:
- Parallel support: IPS systems operate alongside other security solutions, combining and supporting the identification of threats and attacks that other solutions may miss. They provide superior application security due to high application awareness.
- Optimize the effectiveness of other security measures: During operation, IPS systems filter malicious traffic before transmitting data to other security devices and controls. Therefore, IPS minimizes the workload that other security measures have to handle, optimizing time, resources, and processing efficiency.
- Time-saving: IPS systems operate fully automatically, thus optimizing IT manpower and reducing the workload of routine manual tasks.
- Customizability: IPS systems can be configured with security policies tailored specifically to each enterprise using them.
- Protection against known and unknown threats: IPS can block known threats and simultaneously detect and block previously unseen threats.
- Real-time protection: IPS can detect and prevent malicious traffic in real-time, preventing attacks and minimizing any damage.
- Enhanced network visibility: IPS provides network visibility, allowing you to monitor what is happening within your network and identify potential security risks.
5. How does an IPS work?
5.1 Signature-based detection and prevention systems
Designed to detect attacks and potential threats by analyzing and comparing network traffic log data with existing attack patterns. The system takes the necessary action if any intrusion is detected that matches the signatures stored in the database.
5.2 Anomaly-based detection and prevention systems
Designed to accurately identify unknown attacks and new malware. The main benefit of anomaly recognition is that alerts are generated not based on specific attack signatures but on the unusual actions of those attacks.
This allows the system to easily detect attacks before they occur.
6. What is an IDS?
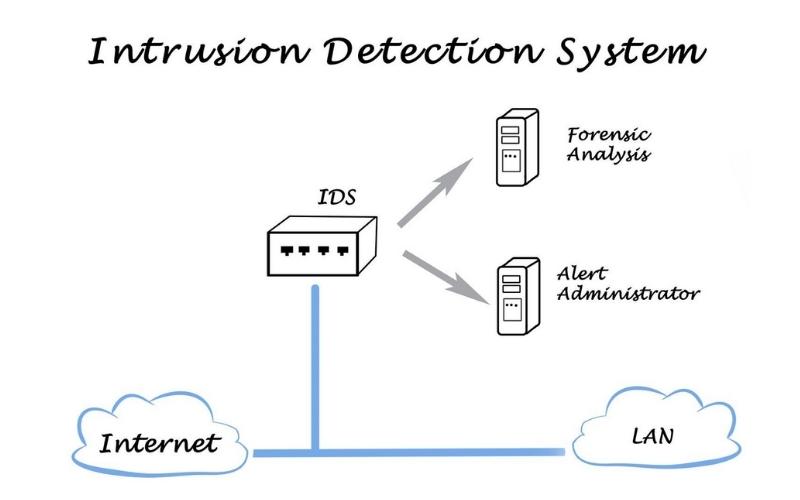
What is an IDS? For those in the industry, this concept is not unfamiliar. However, for businesses just starting to build a data security process, IDS is a very important concept.
IDS stands for Intrusion Detection System - a tool that supports system security and alerts when intrusions occur. Often integrated into other security systems, IDS helps protect system information by detecting and alerting intrusions.
7. What are the important roles of IDS?
After understanding what an IDS is, readers will need to grasp the main roles or tasks of IDS in today's network systems.
IDS has significant features, including:
- Monitoring network traffic and suspicious activities.
- Alerting the system and network administrators about anomalies.
- Integrating with firewall devices and antivirus software to create a comprehensive security system.
8. What are the main functions of IDS?
The Intrusion Detection System (IDS) is an important tool for enhancing network and data security. We have summarized the main functions of IDS to help readers easily visualize:
- The IDS system helps monitor suspicious network traffic and notify network administrators. Given the increasingly sophisticated and frequent cyber-attacks, the role of a comprehensive and effective intrusion detection system is extremely important.
- IDS helps organize important network data and prioritize which activities are more critical. It also saves time, reduces manual effort, and minimizes human errors in intrusion detection.
- IDS helps detect, categorize, and deeply alert about incoming/outgoing network traffic. This helps users save time, optimize manual workload, and minimize errors in intrusion detection by analyzing critical information in thousands of system logs.
- IDS can filter through traffic to detect and prevent intrusions, improving overall network performance and defending against malicious activities. Applying IDS systems optimizes intrusion detection and prevention, saving users time, energy, and resources.
It can be said that the more an IDS system understands and recognizes malicious activities on your network, the better it can adapt to increasingly sophisticated attacks.
9. How does a standard IDS system work?
Overall, a standard IDS system functions as follows:
- The IDS will scan network traffic based on specific attack patterns. The system uses signatures or patterns of known attacks to detect intrusions.
- The system will notify administrators about detected intrusions.
- IDS systems often work alongside other security solutions to create a comprehensive security system.
10. Most common types of IDS today
There are two main types of IDS systems:
- Network-based Intrusion Detection Systems (NIDS): These are the most common types of IDS. They are placed at strategic points within the network to monitor incoming and outgoing traffic. They aim to identify suspicious activities and potential intrusions on the network.
- Host-based Intrusion Detection Systems (HIDS): These systems are installed on specific endpoints (such as servers, workstations) to monitor traffic to and from those hosts, protecting the host from potential threats and providing the last line of defense when the NIDS fails to detect the intrusion.
Understanding what IDS and IPS are and their benefits will help readers, especially businesses, gain more insights into network security issues. Consequently, you will know how to protect your system and data comprehensively against increasingly sophisticated and numerous cyber-attacks. If you are looking for a top-notch, comprehensive network security solution, contact us immediately for a consultation!












