WORK MORE EFFICIENTLY WITH NEXTCLOUD
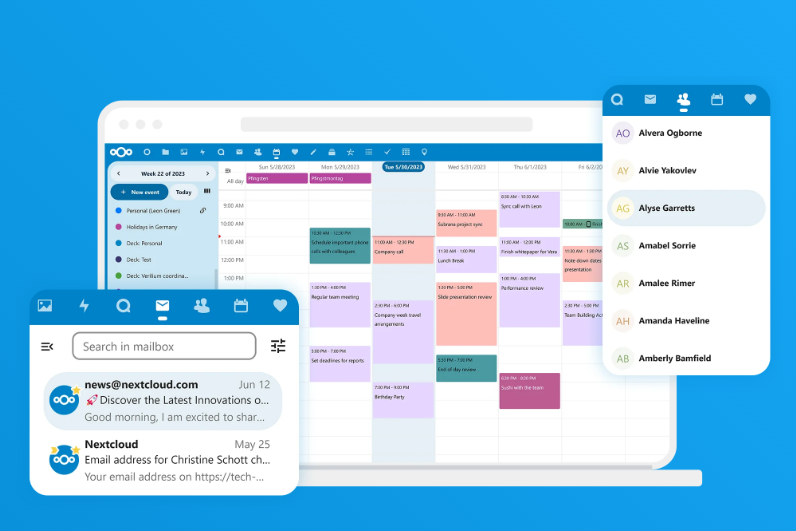
NextCloud Groupware
NextCloud Groupware provides easy-to-use webmail, calendar, and contacts to help your team work faster and more efficiently, integrated with Nextcloud Files.
Advanced notification system.
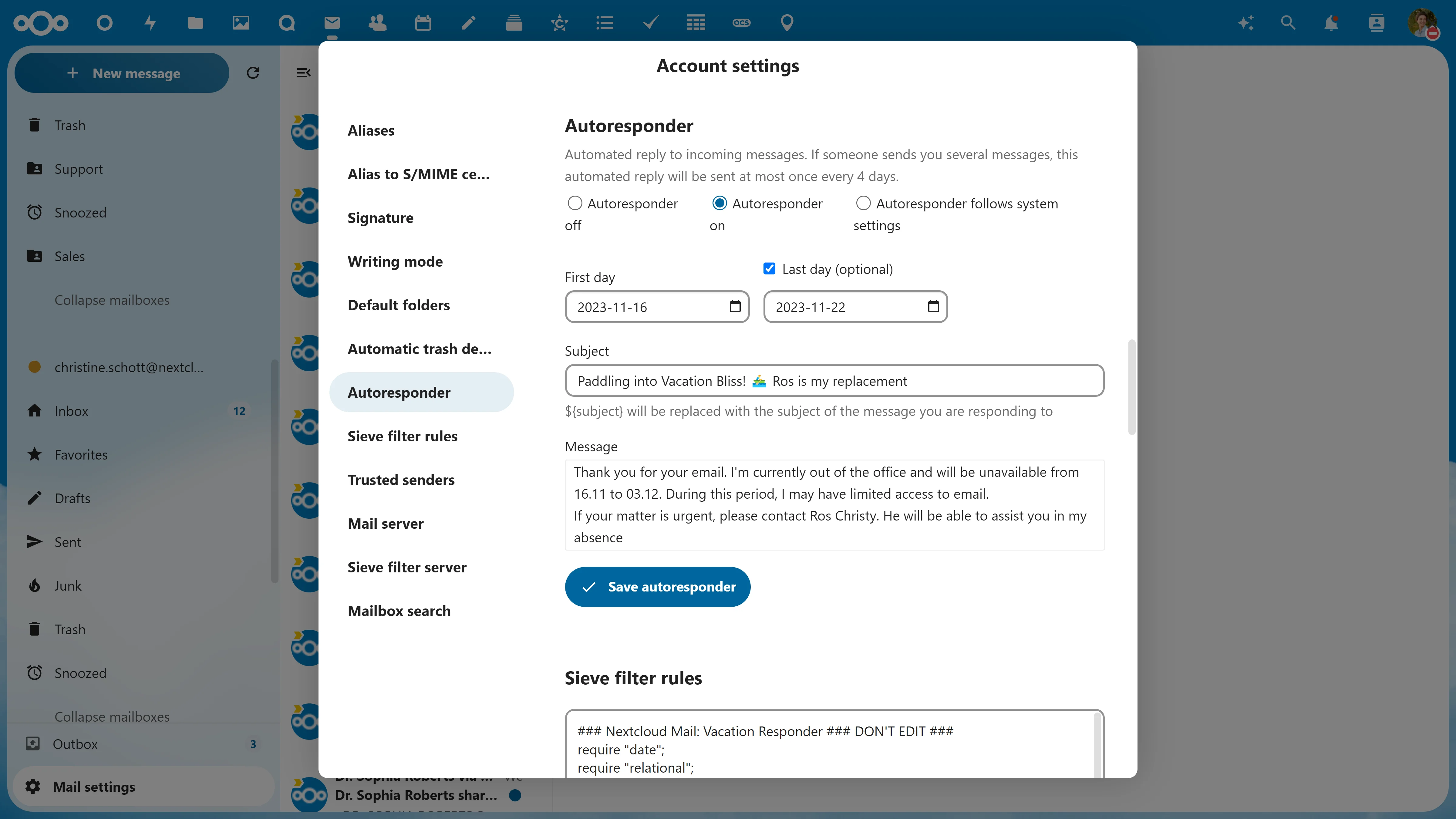
Set an away status to notify everyone in the Hub that you are away and who the substitute contact is.
How to do it:
1. Access the 'Availability' section in your personal settings.
2. Choose your day-off.
3. Configure information:
- Out of Office notification: Let everyone know you're away and when you'll be back.
- Backup contact: Identify someone who can provide support while you're away.
Benefits:
- Your away status will automatically update across the entire platform.
- The auto-reply feature in Email will notify everyone about your absence and when you'll be back.
- The calendar will automatically create an event for your days off.
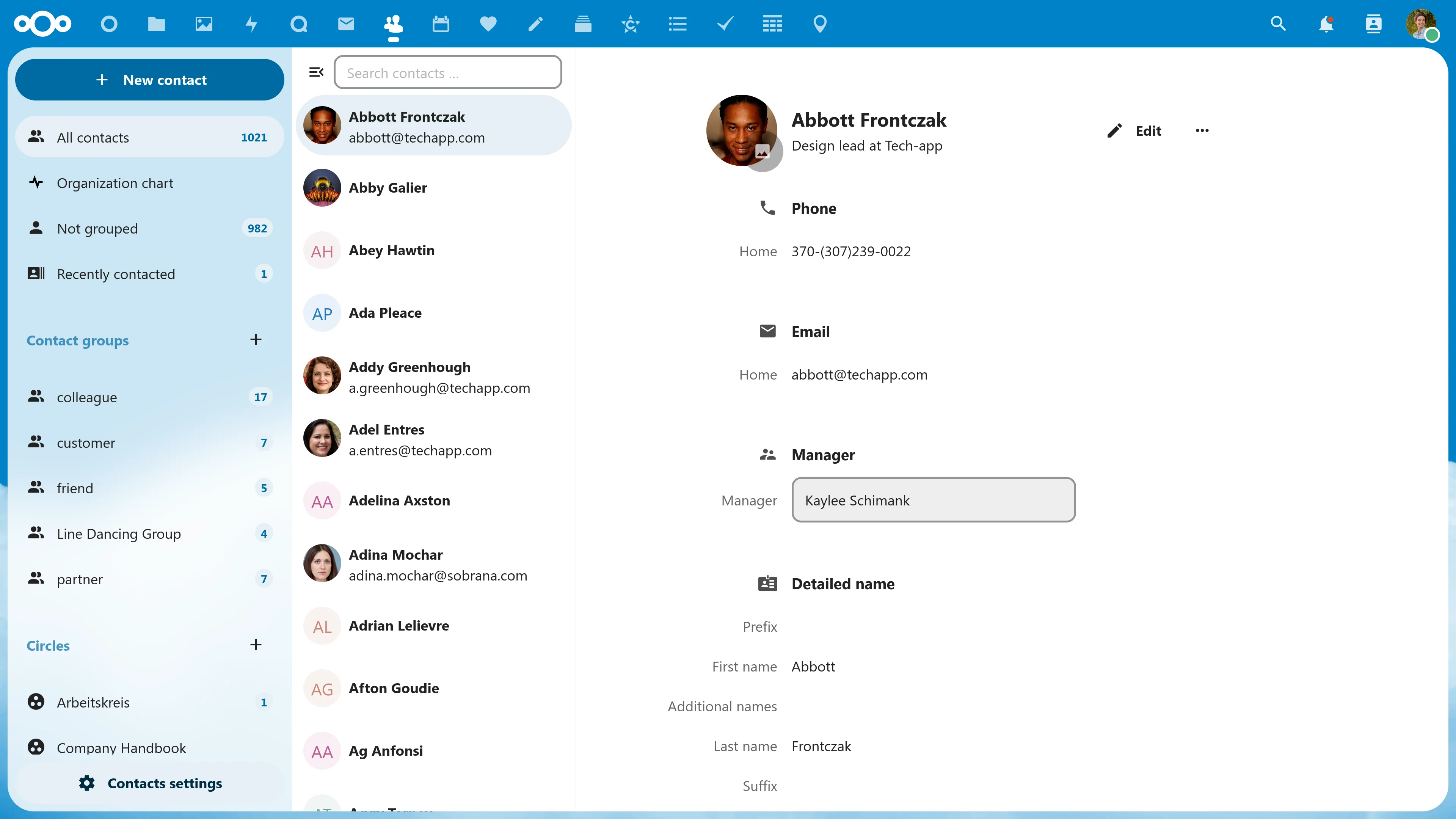
The Hub Contacts app:
Key features:
- Simple and intuitive interface
- Neatly organized contact list
- Easy search and view detailed information of contacts
- Quick and convenient contact information editing
- Switch between single-column and multi-column view modes.
Advantages:
- Increase efficiency in managing contacts.
- Save time searching for contact information.
- Enhance user experience.
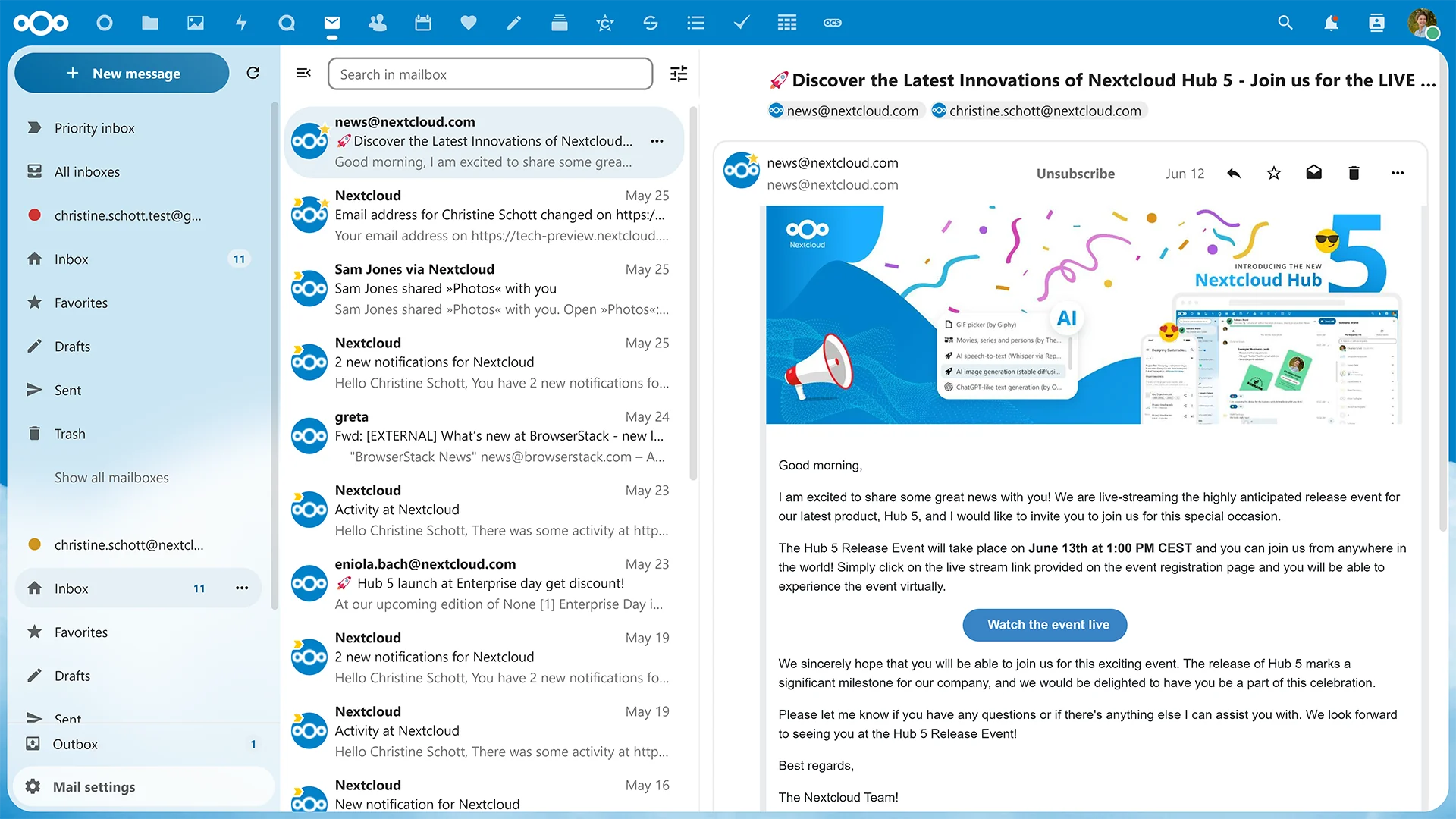
Mail Management
Manage your inbox with options like creating subfolders, sorting subscriptions, and marking emails as read. Fine-tune your mailbox for optimal efficiency.
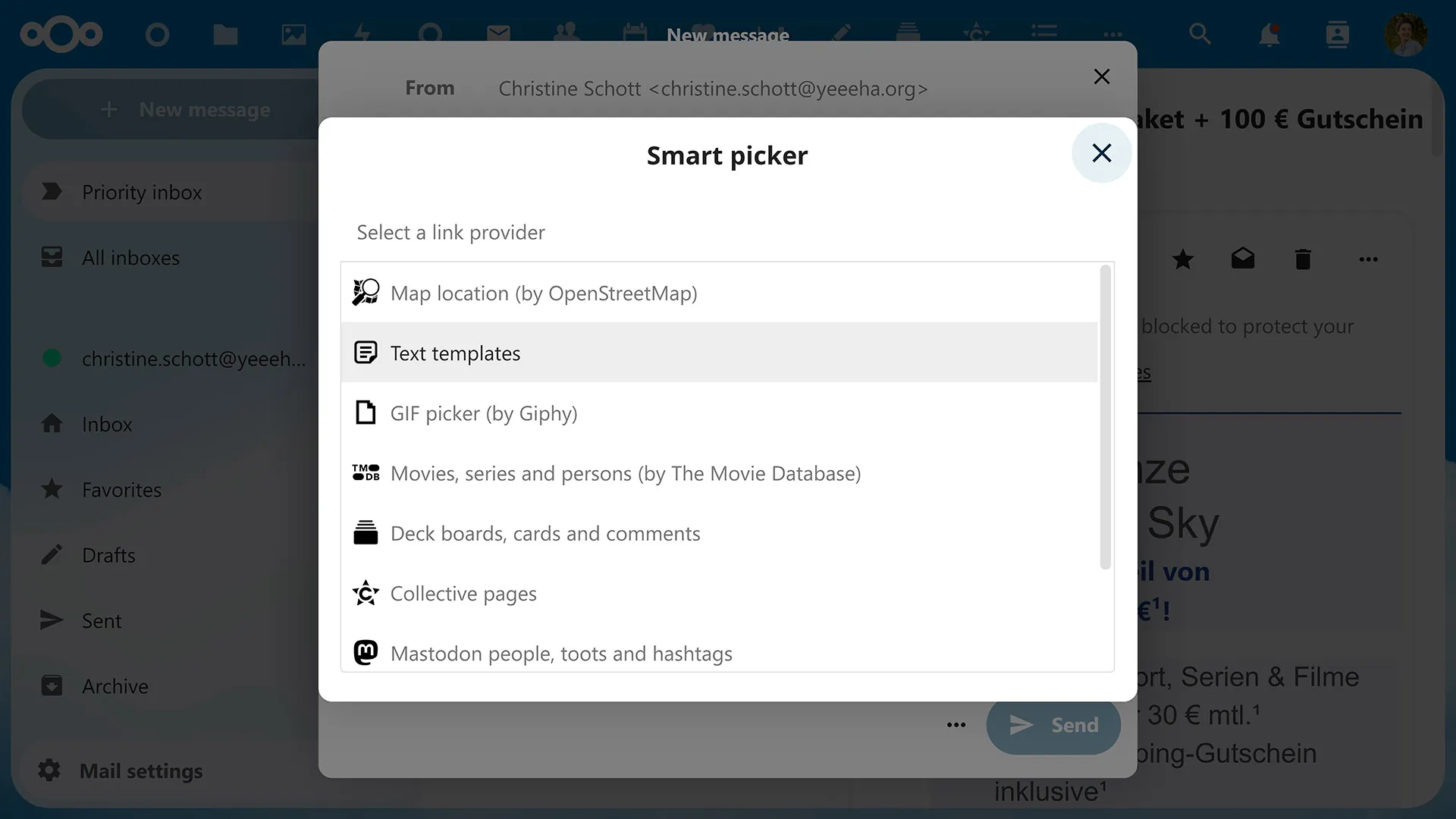
Smart Picker
The best way to introduce our smart, new features is through the Smart Selector - a feature that allows users to utilize AI (and more) in their daily workflow in a personalized way.
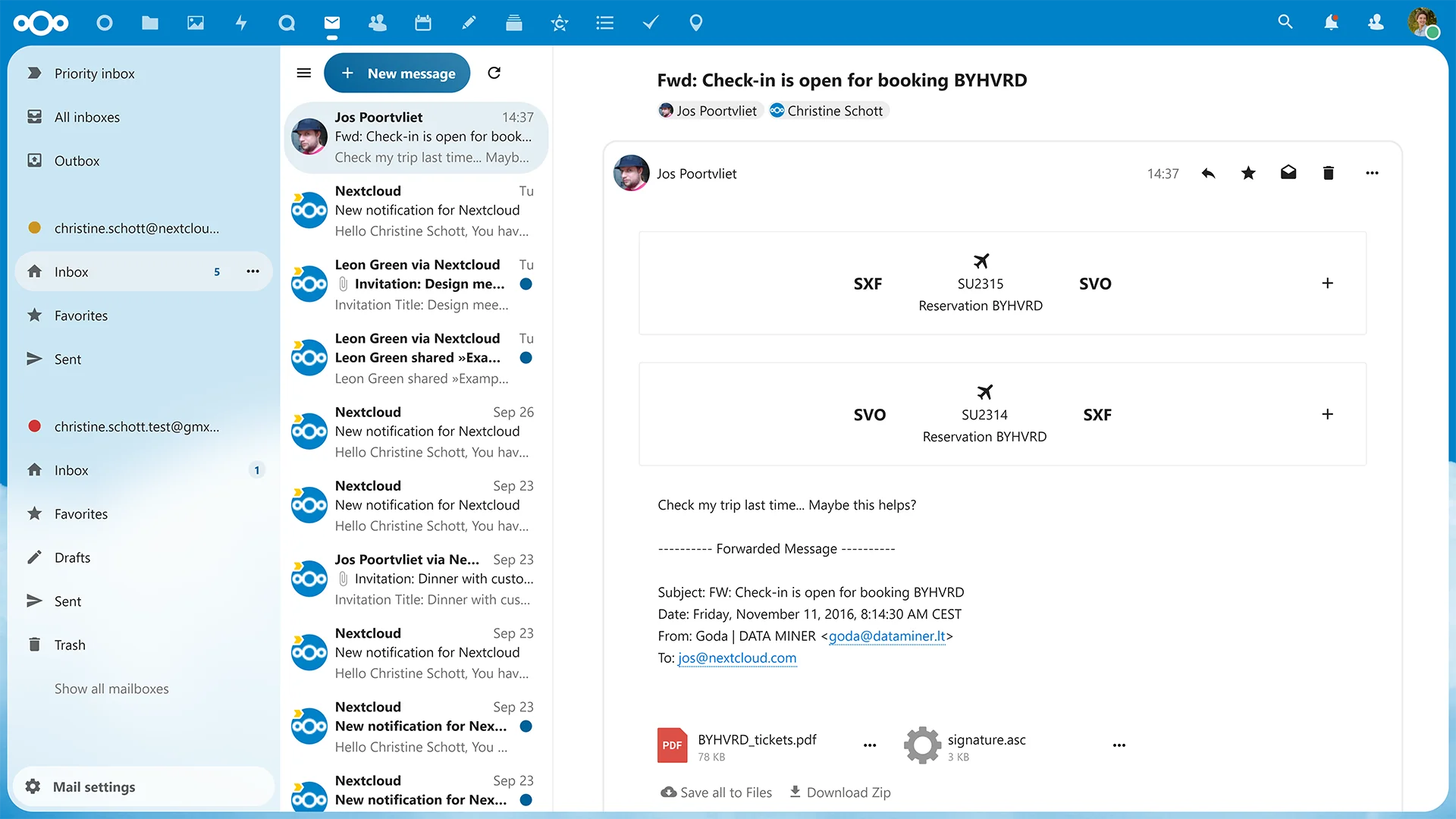
Easily add an itinerary to the Calendar.
Integrate with Microsoft.
Nextcloud Enterprise is designed to integrate well in Microsoft environments, with capabilities for file storage, user directories, Outlook, Sharepoint, Windows Desktop, MS Office online servers, and Teams integration.

Cloud system security
Nextcloud employs various security features to protect user data, including data storage encryption, data transmission encryption, two-factor authentication, and access control. Therefore, users can rest assured that their data is securely protected from hackers and other threats.













